| CPC G06F 3/0619 (2013.01) [G06F 3/0656 (2013.01); G06F 3/0659 (2013.01); G06F 8/65 (2013.01); G06F 21/554 (2013.01); G06F 3/123 (2013.01); G06F 21/50 (2013.01); G06F 21/572 (2013.01)] | 20 Claims |
|
9. A method comprising:
storing, on a non-volatile storage medium of a data storage device:
at least one file system control block, the file system control block comprising a first partition of the non-volatile storage medium configured to store:
firmware of the data storage device; and
at least one reference data structure comprised of records for malicious data; and
in a second partition of the non-volatile storage medium, user data blocks to store user data from a host computer system, wherein:
a device controller in the data storage device controls the at least one file system control block; and
the host computer system controls the user data blocks through storage commands to the data storage device;
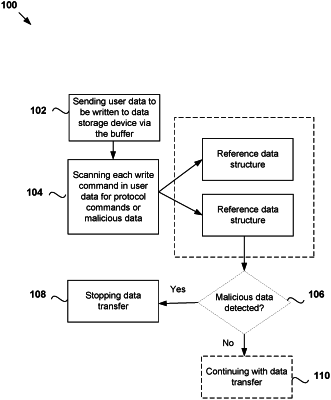
receiving, by the data storage device and from the host computer system, a write command for user data for the user data blocks;
scanning, from a buffer configured to temporarily store user data in the data storage device prior to transferring the user data to the non-volatile storage medium, the user data for the write command to detect protocol commands or malicious data, wherein scanning comprises comparing the user data for the write command to the records in the at least one reference data structure in the first partition; and
stopping the transfer of user data from the buffer to the second partition of the non-volatile storage medium responsive to at least one of protocol commands or malicious data being detected in the user data for the write command.
|