| CPC G06F 21/78 (2013.01) [G06F 21/31 (2013.01); G06F 21/604 (2013.01); G06F 21/6218 (2013.01); G06F 2221/2141 (2013.01)] | 16 Claims |
|
1. A method of multi-level role-based access control for a storage system, the method comprising:
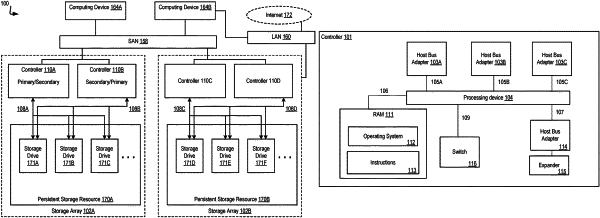
accessing, by an access control system, role permissions configuration data that specifies a plurality of roles and, for a role of the plurality of roles, a first set of permissions that define a first set of permitted operations on types of resources of the storage system and a second set of degraded permissions that define a second set of permitted operations on types of resources of the storage system, wherein the second set of degraded permissions defines the second set of permitted operations to be a subset of the first set of permitted operations defined by the first set of permissions;
identifying, by an access control system from the role permissions configuration data and based on a role of a user requesting access to the storage system, a permission of the role to access a type of resource, wherein identifying the permission of the role to access the type of resource comprises selecting the permission of the role to access the type of resource from either the first set of permissions or the second set of degraded permissions;
determining, by the access control system and based on the type of resource and on a mapping of resources of different secured endpoints of the storage system to types of resources, a set of resources of the storage system that the role has permission to access;
identifying, by the access control system, a subset of the set of resources of the storage system that the user is authorized to access; and
granting, by the access control system, the user role-based access to the subset of the set of resources of the storage system;
wherein the mapping of resources of different secured endpoints of the storage system to types of resources comprises code associated with the resources indicating the types of the resources;
wherein the resources comprise functions of an application program interface (API) configured to be called to interface with storage resources of the storage system.
|