| CPC G06F 21/6245 (2013.01) [H04L 9/0825 (2013.01); H04L 9/0827 (2013.01); H04L 9/088 (2013.01); H04L 9/3213 (2013.01)] | 16 Claims |
|
1. A token handler for securing personally identifiable information, the token handler comprising a memory and a hardware processor communicatively coupled to the memory, the hardware processor configured to:
generate a set of public encryption keys of the token handler;
communicate the set of public encryption keys of the token handler to a data originator;
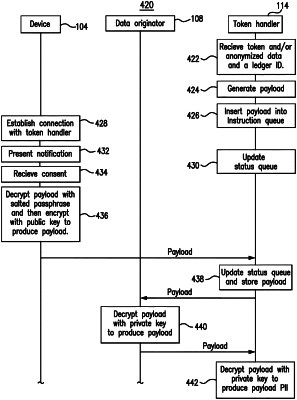
receive, from the data originator, a request to store a user's personally identifiable information, the request to store comprising a first portion of the user's personally identifiable information encrypted using a first public encryption key of the token handler from the set and a second portion of the user's personally identifiable information encrypted using a second public encryption key of the token handler from the set;
add, to an encryption schedule, an indication that the first portion of the user's personally identifiable information was encrypted using the first public encryption key and an indication that the second portion of the user's personally identifiable information was encrypted using the second public encryption key;
receive, from the data originator, a token indicating a request for redemption of the first and second portions of the user's personally identifiable information;
select, based on the encryption schedule, a first private encryption key of the token handler corresponding to the first public encryption key;
decrypt, using the first private encryption key, the first portion of the user's personally identifiable information encrypted using the first public encryption key to produce the first portion of the user's personally identifiable information;
select, based on the encryption schedule, a second private encryption key of the token handler corresponding to the second public encryption key;
decrypt, using the second private encryption key, the second portion of the user's personally identifiable information encrypted using the second public encryption key to produce the second portion of the user's personally identifiable information; and
store a key vault comprising the set of public encryption keys and an ordinal assigned to each key of the set of public encryption keys, wherein the encryption schedule identifies the first public encryption key using the ordinal assigned to the first public encryption key in the key vault.
|