| CPC G06F 21/6245 (2013.01) [G06F 9/45558 (2013.01); G06F 21/57 (2013.01); H04L 9/3236 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01); H04L 9/50 (2022.05)] | 17 Claims |
|
1. A computer implemented method of executing verifiable computation modules to process private data at private data at private data owner platform, comprising:
using at least one processor of a private data owner for:
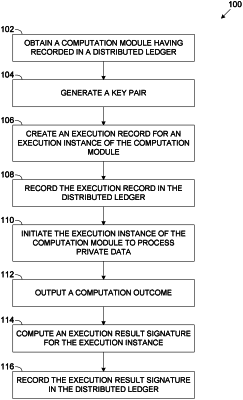
obtaining a computation module having a unique identifier recorded in a distributed ledger controlled by a plurality of computing nodes each maintaining a local copy of the distributed ledger;
generating a key pair comprising a signing key and a verification key derived from the signing key;
recording, in the distributed ledger, an execution record associating an execution instance of the computation module with the verification key;
initiating the execution instance of the computation module to process a private dataset incorporated with the signing key;
outputting a computation outcome;
computing an execution result signature for the execution instance based on the unique identifier and the private data and signing key; and
recording the execution result signature in the distribution ledger to enable verification of the execution instance;
wherein the computation module used to process the private dataset is verifiable based on its identification in the execution record, and the execution instance of the computation module to process the private dataset is:
verifiable based on the execution result signature and the verification key extracted from the execution record, and
repeatable by the at least one processor based on the execution result signature.
|