| CPC G06F 21/565 (2013.01) [G06F 16/13 (2019.01); G06F 16/1734 (2019.01); G06F 16/2246 (2019.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
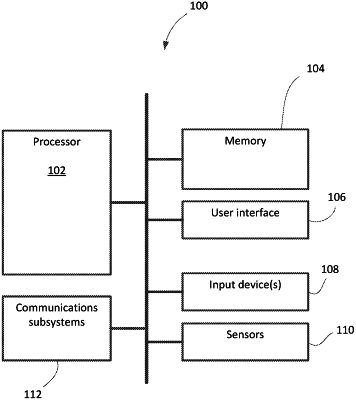
1. A computer-implemented method of determining whether a computing device has been compromised, the computing device having a first profile and a second profile, the method comprising:
based on determining that file tree structure information for the first profile includes information regarding files within the second profile, determining from the file tree structure information for the first profile that the computing device has been compromised; and
based on the determination that the computing device has been compromised, taking an action.
|