| CPC G06F 21/32 (2013.01) [G06Q 20/40145 (2013.01); G06V 40/12 (2022.01); G06V 40/1365 (2022.01); G06V 40/16 (2022.01); H04L 63/0861 (2013.01); G06V 40/179 (2022.01); G06V 2201/10 (2022.01)] | 18 Claims |
|
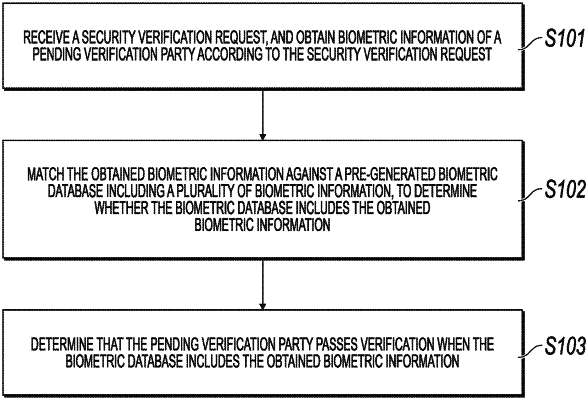
1. A computer-implemented method for multi-factor biometric-based verification of an identity of a user, the method comprising:
obtaining biometric information from the user, wherein the biometric information comprises at least one of a facial feature, an iris feature, or a fingerprint;
obtaining, from the user, a geographical region associated with the user;
determining, from a plurality of biometric databases, one biometric database corresponding to the geographical region to be a first biometric database, wherein the first biometric database comprises a plurality of biometric information corresponding to a plurality of users associated with the geographical region;
determining that the obtained biometric information does not match any entry in the first biometric database;
in response to determining that the obtained biometric information does not match any entry in the first biometric database, determining that the obtained biometric information matches at least one entry in a second biometric database, wherein the second biometric database comprises a second number of entries greater than a first number of entries of the first biometric database;
in response to determining that the obtained biometric information matches at least one entry in the second biometric database, obtaining non-biometric verification information from the user;
determining that the non-biometric verification information matches at least a portion of preset non-biometric verification information associated with the user, wherein a length of the non-biometric verification information is less than a length of the preset non-biometric verification information; and
in response to determining that the non-biometric verification information matches at least a portion of the preset non-biometric verification information associated with the user, determining that the identity of the user is verified.
|