| CPC H04W 12/106 (2021.01) [H04W 12/02 (2013.01); H04W 12/069 (2021.01); H04W 72/20 (2023.01)] | 24 Claims |
|
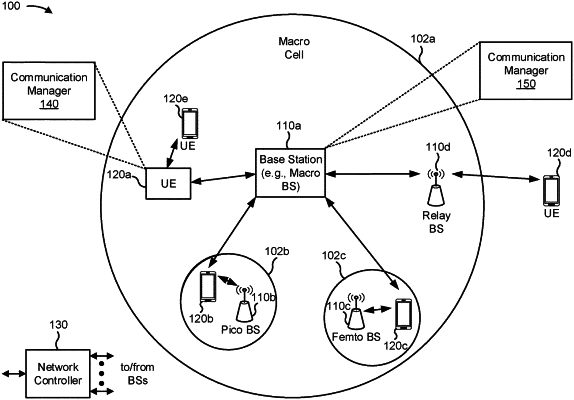
1. A method of wireless communication performed by a receiver user equipment (UE), comprising:
receiving at least one control communication that includes a first part and a second part;
determining an authenticity status of the at least one control communication based at least in part on at least one message authentication code (MAC), the MAC is based at least in part on a common security key corresponding to the first part or a private security key corresponding to the second part, the at least one control communication includes a first sidelink control information (SCI) communication and a second SCI communication, and the at least one MAC includes a first MAC corresponding to the first SCI communication and a second MAC corresponding to the second SCI communication; and
performing a wireless communication task based at least in part on the authenticity status of the at least one control communication.
|