| CPC H04L 63/1475 (2013.01) [G06F 18/2411 (2023.01); G06N 3/04 (2013.01); G06V 10/764 (2022.01); G06V 10/774 (2022.01); G06V 10/776 (2022.01); H04L 63/0485 (2013.01); H04L 63/18 (2013.01)] | 9 Claims |
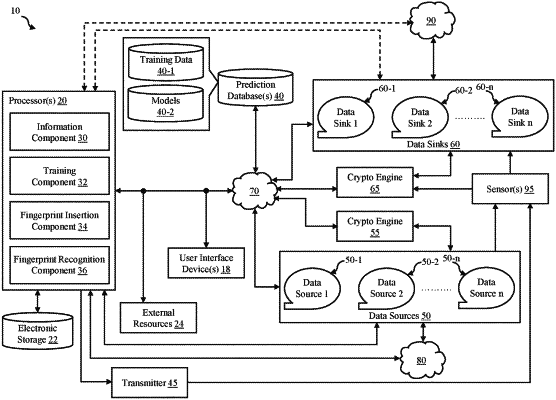
|
1. A computer-implemented method comprising:
generating a data set configured to have a first amount of entropy;
before cryptographic encryption of user data, combining the user data with the generated data set;
obtaining, from a network, (i) a first ciphertext resulting from cryptographic encryption of the combined data and (ii) a plurality of second ciphertexts located in the network;
determining, via a machine learner, an entropy level of the first ciphertext;
determining, via the machine learner, an entropy level of each of the plurality of second ciphertexts;
determining, via the machine learner, whether the entropy level of the first ciphertext is greater than the entropy level of each of the second ciphertexts;
responsive to the determination that the first ciphertext has the greater amount of entropy, identifying a portion of the network traversed by the first ciphertext; and
outputting, to a user remote from the network, the portion.
|