| CPC H04L 63/1441 (2013.01) [H04L 63/123 (2013.01)] | 18 Claims |
|
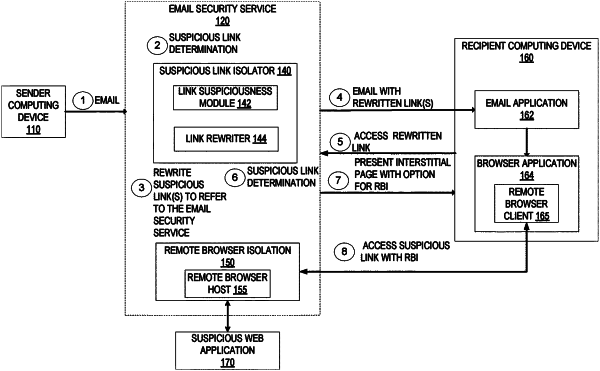
1. A method to isolate suspicious email links performed by an email security service, comprising:
receiving an email that includes a first link that refers to a first external resource and further includes a second link to a second external resource, the email intended for a recipient;
performing a first suspicious link determination to determine whether the first link is suspicious, wherein a first result of the first suspicious link determination is that the first link is suspicious;
responsive to the first result of the first suspicious link determination, rewriting the first link to refer to the email security service such that responsive to the first link being opened, a request is transmitted to the email security service and not to the first external resource;
performing the first suspicious link determination to determine whether the second link is suspicious, wherein a second result of the first suspicious link determination is that the second link is not suspicious;
delivering the email with the rewritten first link and the second link that is not rewritten to the recipient;
receiving a first request from a client device responsive to the first link being opened;
performing a second suspicious link determination to determine whether the first link is suspicious, wherein a first result of the second suspicious link determination is that the first link is suspicious; and
responsive to the first result of the second suspicious link determination, transmitting an interstitial page to the client device that includes an option that, when selected, causes the first link to be opened in a remote browser isolation session.
|