| CPC H04L 63/123 (2013.01) [H04L 9/3247 (2013.01)] | 22 Claims |
|
1. A computer-implement method comprising:
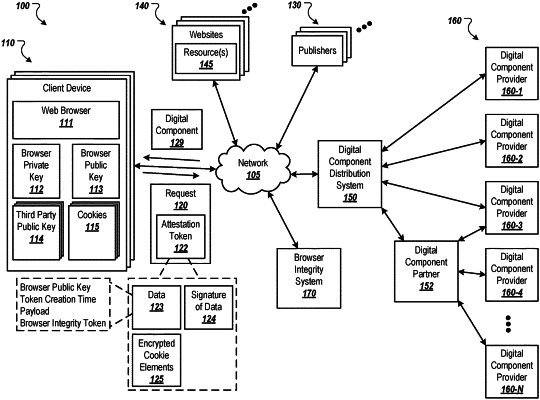
receiving, from an application of a client device, a request including an attestation token of the application, the attestation token including:
a set of data that includes at least a public key of the application and a token creation time that indicates a time at which the attestation token was created;
a signature of the set of data, wherein the signature was generated using a private key that corresponds to the public key; and
a group of encrypted cookie elements that includes, for each of a plurality of recipients of the request, a respective encrypted cookie element that includes an encrypted result from encrypting a cookie of the recipient that is stored on the client device using a public key of the recipient, wherein the respective encrypted cookie element for each recipient is different from the respective encrypted cookie element for each other recipient; and
verifying an integrity of the request using the attestation token, including:
determining whether the token creation time is within a threshold duration of a time at which the request was received;
determining, using the public key and the signature of the set of data generated using the private key, whether the set of data was modified after the attestation token was created; and
determining that the integrity of the request is valid based at least on determination that the token creation time is within the threshold duration of the time at which the request was received and a determination that the set of data has not been modified since the attestation token was created; and
responding to the request in response to determining that the integrity of the request is valid.
|