| CPC H04L 63/0884 (2013.01) [G06F 11/3006 (2013.01); G06F 11/3438 (2013.01); G06F 11/3476 (2013.01); G06F 16/24547 (2019.01); G06F 21/31 (2013.01); G06F 21/604 (2013.01); G06F 21/6227 (2013.01); G06F 21/6254 (2013.01); H04L 63/0281 (2013.01); H04L 63/101 (2013.01); H04L 63/102 (2013.01); H04L 63/104 (2013.01); H04L 63/105 (2013.01); H04L 63/1425 (2013.01); H04L 63/166 (2013.01); H04L 63/168 (2013.01); H04L 69/326 (2013.01); H04L 69/329 (2013.01); G06F 2221/2107 (2013.01); H04L 67/01 (2022.05); H04L 2463/082 (2013.01)] | 17 Claims |
|
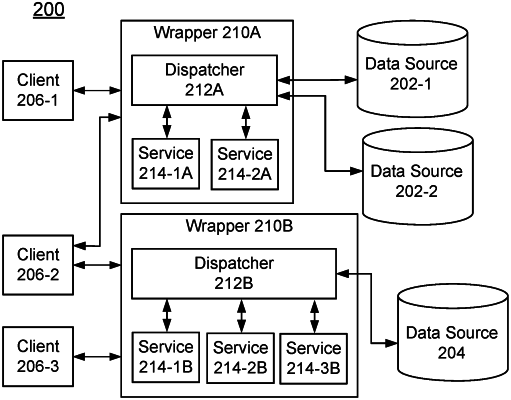
1. A method, comprising:
receiving a query for a data source at a wrapper, the wrapper including a dispatcher and a service, the dispatcher receiving the query and being data agnostic;
providing the query from the dispatcher to the data source and to the service; and
analyzing the query using the service, comprising:
parsing the query;
providing a logical structure based on the query; and
analyzing the logical structure, comprising:
performing one or more of the following:
A) determining that the query adversely affects performance; and
in response to a determination that the query adversely affects performance, rewriting the query to remove an “OR” clause, a tautology, or both from the query; and/or
B) determining that the query is an attack, comprising:
determining that the query includes wildcards in users' names and/or tautologies in users' names; and
in response to a determination that the query includes wildcards in the users' names and/or tautologies in the users' names, determining that the query is the attack;
in response to a determination that the query is an attack, preventing access to the data source, comprising:
terminating a connection to a client from which the query originated.
|