| CPC H04L 51/212 (2022.05) [G06F 21/313 (2013.01)] | 15 Claims |
|
1. A method, comprising:
storing, at an email verification system, a plurality of names and a plurality of email addresses, wherein each name of the plurality of names is associated with an email address of the plurality of email addresses;
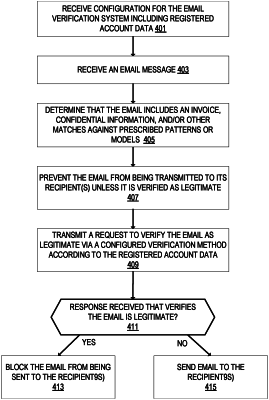
receiving, at an email verification system, a first email having a first sender name and a first sender email address;
determining that the first sender name of the first email matches a first name of the stored plurality of names, and that the first sender email address of the first email does not match with a first email address of the stored plurality of email addresses associated with the first name, and responsive to this determination, preventing the first email from being transmitted to its recipient unless the first email is verified as being legitimate;
transmitting a first request to verify the first email as being legitimate via a first configured verification method, wherein the first configured verification method is one of: email verification, text message verification, authentication application verification, and phone call verification, and wherein the first request to verify the first email as being legitimate includes a second email being sent to the first email address;
receiving a first response to the first request that verifies the first email as being legitimate;
transmitting the first email to its recipient responsive to the receiving the first response;
receiving, at the email verification system, a third email having a second sender name and a second sender email address;
determining that the second sender name of the third email matches a second name of the stored plurality of names, and that the second sender email address of the third email does not match with a second email address of the stored plurality of email addresses associated with the second name, and responsive to this determination, preventing the third email from being transmitted to its recipient unless the third email is verified as being legitimate;
transmitting a second request to verify the third email as being legitimate via a second configured verification method, wherein the second configured verification method is one of: email verification, text message verification, authentication application verification, and phone call verification, and wherein the second request to verify the third email as being legitimate includes a fourth email being sent to the second email address;
receiving a second response to the second request that indicates that the third email is not legitimate; and
blocking the third email from being sent to its recipient.
|