| CPC G06V 30/19173 (2022.01) [G06F 18/214 (2023.01); G06F 18/241 (2023.01); G06N 20/00 (2019.01); H04L 51/08 (2013.01); H04L 51/212 (2022.05); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1483 (2013.01)] | 20 Claims |
|
1. A method comprising:
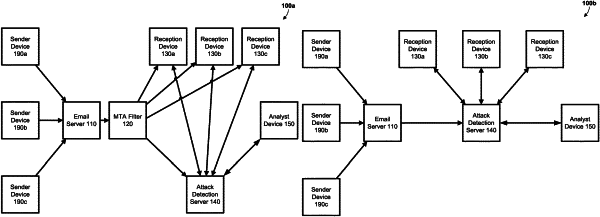
receiving an email addressed to a user;
separating the email into a plurality of email components including a first link;
analyzing, using machine-learning techniques, the first link by:
virtually navigating to an end-point of the first link;
receiving any automatic download triggered by virtually navigating to the end-point; and
analyzing the automatic download;
providing the analyses of the first link to a stacked ensemble analyzer comprising a nonparametric model; and
determining, based on an output of the stacked ensemble analyzer, that the email is potentially malicious.
|