| CPC G06Q 20/4014 (2013.01) [G06F 21/33 (2013.01); G06F 21/335 (2013.01); G06F 21/34 (2013.01); G06F 21/35 (2013.01); G06F 21/6218 (2013.01); G06K 19/06037 (2013.01); G06Q 20/02 (2013.01); G06Q 20/24 (2013.01); G06Q 20/26 (2013.01); G06Q 20/3223 (2013.01); G06Q 20/3224 (2013.01); G06Q 20/3274 (2013.01); G06Q 20/38215 (2013.01); G06Q 20/385 (2013.01); G06Q 20/4015 (2020.05); H04L 9/3226 (2013.01); G06F 2221/2111 (2013.01); G06Q 2220/00 (2013.01); H04L 2209/56 (2013.01); H04L 2209/80 (2013.01)] | 20 Claims |
|
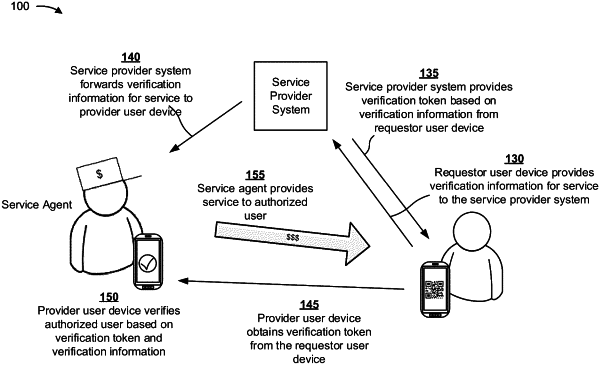
1. A method, comprising:
receiving, by a first device and from a second device, a request for a service, wherein receiving the request further comprises receiving verification information associated with the request for the service;
identifying, by the first device, a third device to facilitate providing the service;
encrypting, by the first device, the verification information using a time period,
wherein the time period is associated with an interaction between the second device and the third device for the service;
dynamically generating, by the first device, a verification token using the encrypted verification information and a characteristic associated with the second device,
wherein the characteristic associated with the second device is based on the interaction, and
wherein the characteristic is associated with the time period;
transmitting, by the first device and to the second device, the verification token, wherein the verification token is sent by the second device to the third device to be decrypted;
transmitting, by the first device and to the third device, the verification information;
receiving, by the first device and from the third device, a confirmation indicating that a decrypted version of the verification token is verified by the third device based on the third device decrypting the verification token and verifying the decrypted version of the verification token with the verification information, wherein the decrypted version of the verification token is verified based on the verification token being decrypted by the third device within a threshold time period based on the time period; and
processing, by the first device and based on the confirmation, a transaction, associated with the service.
|