| CPC G06Q 10/0635 (2013.01) [G06F 21/552 (2013.01); G06F 21/6245 (2013.01); G06N 20/00 (2019.01); H04L 63/1433 (2013.01); H04L 63/205 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
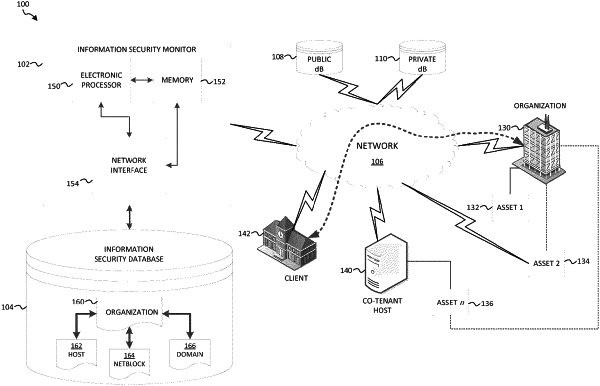
1. A method for assessing information technology risk priorities for network computer systems/assets, the method comprising:
receiving, by an electronic processor, a network identifier associated with a network-accessible computer system/asset of an organization;
accessing, via a network, a set of network-accessible computer systems/assets, including the network-accessible computer system/asset and a plurality of related network-accessible computer systems/assets;
determining indicia of content features/characteristics for each of a subset of the set of the network-accessible computer systems/assets;
determining indicia of security features/characteristics of each of the subset of the set of the network-accessible computer systems/assets;
determining network proximity between respective network-accessible computer systems/assets;
assigning a value at risk for each of the subset of the network-accessible computer systems/assets based on a combination of the indicia of content features/characteristics, the indicia of security features/characteristics, and the network proximity between network-accessible computer systems/assets, wherein the value at risk represents a measure of relative organizational risk exposure or loss potential in an event of compromise of a respective network-accessible computer system/asset; and
automatically prioritizing allocation of security controls/measures among the subset of the network-accessible computer systems/assets based on respective assigned values at risk.
|