| CPC G06F 9/5016 (2013.01) | 15 Claims |
|
1. A computing device comprising:
a memory including:
a system management (SM) memory segment to store information regarding a processor in normal operation of an operating system of the computing device;
an operating system memory segment to store a set of signatures of known process pool tags, wherein a known process pool tag identifies a process implemented in normal operation of the operating system; and
a firmware controller communicatively coupled to the memory, wherein the firmware controller is to:
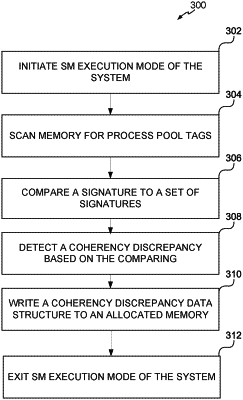
initiate a SM execution mode of the computing device in response to an interruption to the normal operation of the operating system;
scan the operating system memory segment to detect a process pool tag;
generate a signature for the process pool tag that is detected;
compare the signature generated for the process pool tag to the set of signatures of known process pool tags;
detect a coherency discrepancy from comparing the signature generated for the process pool tag and the set of signatures of known process pool tags, wherein the coherency discrepancy indicates a presence of malware on the computing device;
store the coherency discrepancy in the operating system memory segment for access by the operating system following exit from the SM execution mode; and
exit the SM execution mode.
|