| CPC G06F 21/554 (2013.01) [G06F 21/128 (2013.01); G06F 21/54 (2013.01); G06F 9/45529 (2013.01); G06F 9/54 (2013.01); G06F 2221/033 (2013.01)] | 41 Claims |
|
1. A cyber security system, comprising:
at least one processor configured to:
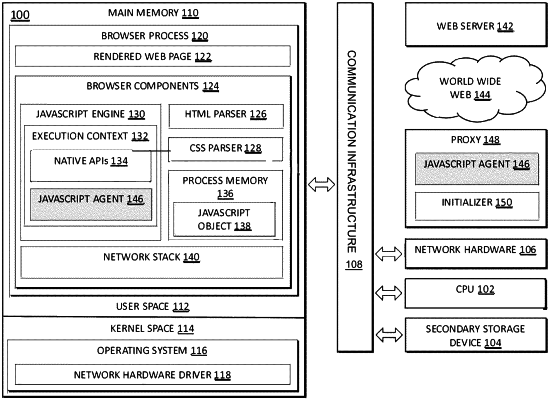
receive, by an application capable of JavaScript execution, code executable by a web browser;
execute, before execution of the received code executable by the web browser, an intercepting code, wherein the intercepting code is configured to intercept at least one application programming interface (API) invocation by the received code executable by the web browser;
intercept, by the intercepting code, an API invocation by the received code executable by the web browser;
determine that the intercepted API invocation results in a manipulation of a first backing store object in browser process memory; and
modify an execution of the intercepted API invocation, wherein the modified execution of the intercepted API invocation results in at least one of: a non-predictable memory layout, a non-predictable memory behavior, or a non-predictable property of the first backing store object or a second backing store object.
|