| CPC G06F 11/3692 (2013.01) [G06F 8/60 (2013.01); G06F 8/70 (2013.01); G06F 11/3608 (2013.01)] | 20 Claims |
|
8. A method comprising:
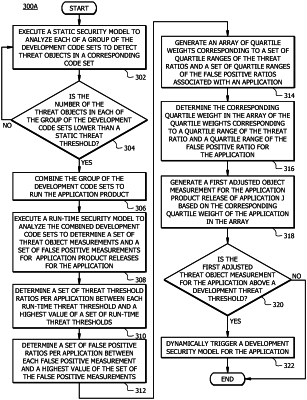
executing a static security model to analyze each of a group of development code sets to detect a number of corresponding threat objects in each of the development code sets;
determining whether the number of the threat objects detected in each development code set is lower than a corresponding static threat threshold;
in response to determining that the number of the corresponding threat objects in each of the group of the development code sets is lower than the corresponding static threat threshold, combining the group of the development code sets, to generate combined development code sets, to run an application;
in response to running the application, executing a run-time security model to analyze the combined development code sets to determine a set of threat object measurements and a set of false positive measurements for a plurality of application product releases for the application, wherein each of the threat object measurements represents a number of threat objects detected in each of the application product releases for the application, and wherein each of the false positive measurements represents a number of false positive threat objects detected in a corresponding application product release;
for each of the application product releases, determining a set of threat threshold ratios between a run-time threat threshold and a highest value of a set of run-time threat thresholds;
for each of the application product releases, determining a set of false positive ratios between each of the false positive measurements and a highest value of the set of the false positive measurements;
generating an array of quartile weights corresponding to a set of quartile ranges of the threat threshold ratios and a set of quartile ranges of the false positive ratios associated with the application;
generating a first adjusted threat object measurement of the application product releases for the application based on a corresponding quartile weight of the application in the array; and
determining, based on the first adjusted threat object measurement, whether to trigger a development security model for the application.
|