| CPC G06F 11/3636 (2013.01) [G06F 8/71 (2013.01); G06F 11/3612 (2013.01); G06F 11/3616 (2013.01)] | 20 Claims |
|
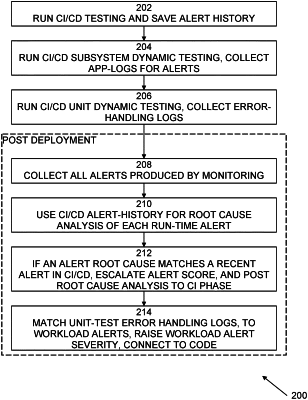
1. A method, implemented in a computer system comprising a processor, a memory accessible by the processor, and computer program instructions stored in the memory and executable by the processor, the method comprising:
generating a first performance and security information relating to a software system during a development of the software system, wherein generating the first performance and security information relating to the software system during the development of the software system comprises performing a static and dynamic testing of code of the software system during the development of the software system to generate a history of one or more generated alerts;
generating a second performance and security information relating to the software system during a deployed operation of the software system;
matching the first performance and security information relating to the software system generated during the development of the software system with the second performance and security information relating to the software system generated during the deployed operation of the software system to determine one or more performance and security alerts to escalate; and
reporting the one or more escalated performance and security alerts.
|