| CPC H04W 12/122 (2021.01) [G16Y 30/10 (2020.01); H04L 43/0829 (2013.01); H04L 43/16 (2013.01); H04L 63/1416 (2013.01); H04W 4/70 (2018.02); H04W 24/08 (2013.01); H04W 64/00 (2013.01); H04L 2463/143 (2013.01); H04W 84/18 (2013.01)] | 20 Claims |
|
1. A device comprising:
one or more processors; and
one or more non-transitory computer-readable media storing instructions that, when executed by the one or more processors, cause the one or more processors to perform operations comprising:
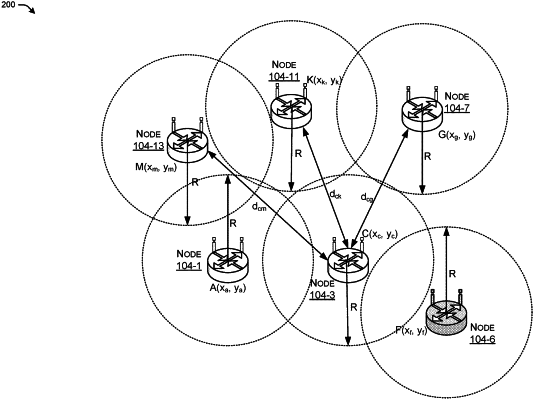
determining a number of drops of a plurality of messages sent to a first node of a plurality of nodes within a mesh network;
based at least in part on the number of drops of the plurality of messages exceeding a threshold number of drops for a time period, decrementing a first rating assigned to the first node to a second rating assigned to the first node;
based at least in part on the second rating being below a rating threshold, determining that the first node is a potentially malicious node;
receiving second location information indicating a second location of a second node;
determining a distance threshold based at least in part on a second distance determined using the second location information;
based at least in part on a first distance to the device calculated based on coordinate information provided by the first node being larger than the distance threshold, identifying that the first node is a malicious node; and
ending communications with the first node.
|