| CPC H04L 63/10 (2013.01) [H04L 63/20 (2013.01); H04L 63/101 (2013.01); H04L 63/205 (2013.01)] | 17 Claims |
|
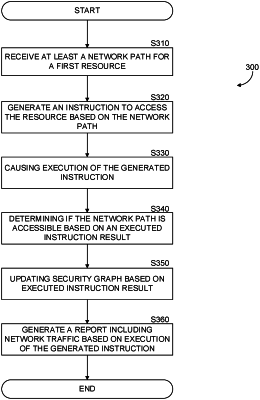
1. A method for performing authorization based active inspection of network paths for a resource, deployed in a cloud computing environment, comprising:
receiving at least one network path to access the resource, wherein the resource is a cloud object deployed in the cloud computing environment, and potentially accessible from an external network which is external to the cloud computing environment;
actively inspecting the at least one network path by an active inspector deployed in an inspection computing environment to determine if the resource is accessible by the active inspector through the at least one network path from the external network, wherein the active inspector includes a processing circuitry, a memory coupled to the circuitry, and a network interface for accessing the external network;
generating an access instruction of a first type to access the resource based on a reachability parameter designated in the at least one network path;
generating another instruction of a second type to access the resource;
executing the generated access instruction and the generated another instruction;
determining the at least a network path is accessible from a network external to the cloud computing environment when the executed instruction and the executed another instruction do not return an error; and
determining that the resource is accessible through the at least one network path and requires access authorization.
|