| CPC H04L 63/0428 (2013.01) [G06F 16/285 (2019.01); H04L 9/30 (2013.01); H04L 63/029 (2013.01)] | 20 Claims |
|
1. A method, comprising:
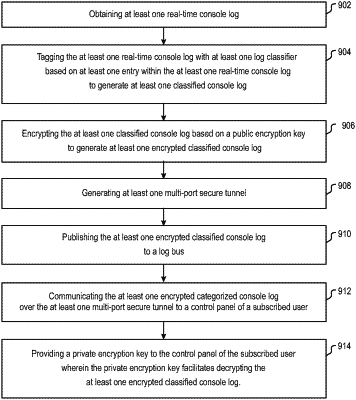
obtaining, by a processor set, at least one real-time console log from a compute instance;
tagging, by the processor set, the at least one real-time console log with at least one log category based on at least one entry within the at least one real-time console log;
generating, by the processor set, at least one categorized console log;
generating, by the processor set, at least one encrypted categorized console log based on a public encryption key;
publishing, by the processor set, the at least one encrypted categorized console log to a log bus;
communicating, by the processor set, the at least one encrypted categorized console log over at least one multi-port secure tunnel to a user terminal device of a subscribed user; and
publishing, by the processor set, a private encryption key to the user terminal device of the subscribed user wherein the private encryption key facilitates decrypting the at least one encrypted categorized console log.
|