| CPC G06Q 20/4016 (2013.01) [G06Q 20/3825 (2013.01); G06Q 20/409 (2013.01)] | 20 Claims |
|
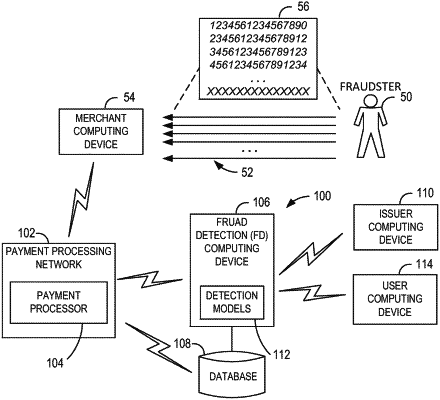
1. A computing system for detecting compromised merchants in a payment card network, the computing system comprising:
at least one processor in communication with at least one memory; and
the at least one memory storing instructions, that when executed by the at least one processor, cause the at least one processor to perform the steps of:
storing historical key merchant variable values for each of a plurality of merchants in the at least one memory;
receiving current transaction data associated with a plurality of current transactions from a merchant of the plurality of merchants, wherein the plurality of current transactions comprises test transactions of payment accounts;
determining, based upon the current transaction data, current key merchant variable values for the merchant;
identifying, in real-time, abnormalities between the current key merchant variable values and the historical key merchant variable values for the merchant;
determining, based upon the identified abnormalities, that the merchant is a compromised merchant and the test transactions processed at the compromised merchant are fraudulent and associated with a security breach;
identifying a compromised merchant computing system associated with the compromised merchant;
identifying, based on the identified compromised merchant computing system, at least one of code fixes and security patches tailored to address the security breach associated with the fraudulent test transactions; and
deploying the at least one of code fixes and security patches to the compromised merchant computing system to address the security breach associated with the fraudulent test transactions.
|