| CPC G06Q 20/3821 (2013.01) [G06Q 20/40 (2013.01); G06Q 20/405 (2013.01); H04L 63/083 (2013.01)] | 16 Claims |
|
1. An apparatus comprising:
a processor; and
a computer readable medium coupled to the processor, the computer readable medium comprising code, executable by the processor for implementing a method comprising,
in a first activation mode,
activating, by the apparatus, a first set of credentials including a first unique identifier and one or more first verification data elements associated with the first unique identifier, and,
after activating the first set of credentials, making the first set of credentials available for use in at least one subsequent transaction, during which, in response to receiving authorization from a first user, the apparatus transmits, from the first set of credentials including the first unique identifier and at least one of the one or more first verification data elements to a transaction processing system; and
in a second activation mode;
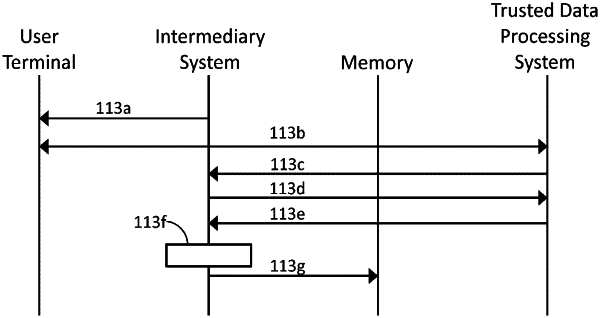
receiving data from a second user terminal operated by a second user via a data communications network,
requesting user input for a second unique identifier from the second user,
initiating an authentication process for the second user, by transmitting a message to the second user terminal to cause a trusted data processing system to authenticate the second user,
receiving, a notification that the second user was successfully authenticated by the trusted data processing system, and
responsive to the second user successfully authenticating during the authentication process, requesting one or more second verification data elements from the trusted data processing system;
receiving the one or more second verification data elements from the trusted data processing system; and
activating a second set of credentials including the second unique identifier and the one or more second verification data elements associated with the second unique identifier, wherein the one or more second verification data elements were received via the data communications network from the trusted data processing system remote from the second user.
|