| CPC H04L 9/3234 (2013.01) [G06Q 20/204 (2013.01); G06Q 20/3226 (2013.01); G06Q 20/3278 (2013.01); G06Q 20/352 (2013.01); G06Q 20/40 (2013.01); H04L 9/0866 (2013.01); H04L 9/14 (2013.01); H04L 9/3228 (2013.01); H04L 9/3242 (2013.01); H04L 63/0853 (2013.01)] | 20 Claims |
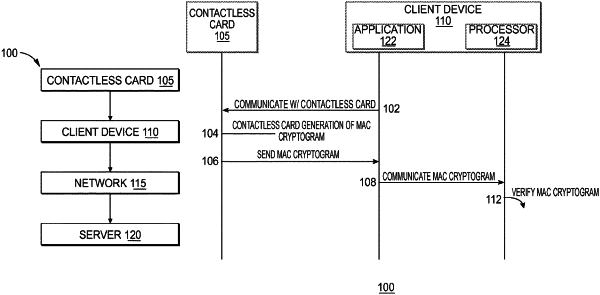
|
1. A contactless card, comprising:
a substrate;
a memory containing a first card key generated based on a first master key and a second card key generated based on a second master key; and
a processor,
wherein the processor is configured to:
generate a first session key using the first card key,
generate a second session key using the second card key,
generate a cryptogram using the first session key, and
encrypt the cryptogram using the second session key.
|