| CPC H04L 9/0631 (2013.01) [G09C 1/00 (2013.01); H04L 9/0637 (2013.01); H04L 9/0643 (2013.01); H04L 9/3236 (2013.01); H04L 2209/046 (2013.01); H04L 2209/12 (2013.01)] | 20 Claims |
|
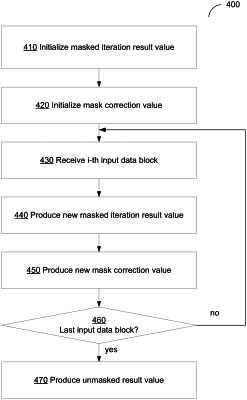
1. A method for performing a cryptographic operation, the method comprising:
receiving, by a processing device, an input data block and an unmasked result value;
multiplying a mask value by a combination of the input data block and the unmasked result value to produce a mask correction value;
multiplying a masked hash key by the combination of the input data block and the unmasked result value to produce a masked result value;
determining a new unmasked result value by applying the mask correction value to the masked result value; and
protecting the cryptographic operation from external monitoring attacks by utilizing the new unmasked result value as a value of a polynomial hash function in the cryptographic operation.
|