| CPC H04L 63/0227 (2013.01) [H04L 63/14 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01); H04L 41/069 (2013.01)] | 19 Claims |
|
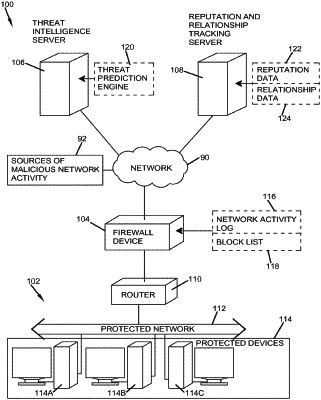
1. A method of predicting network threats, the method comprising:
identifying a first online element as a threat vector from network activity log data based on reputation information of online elements using one or more computing devices, wherein the first online element comprises an internet protocol address;
analyzing relationship data for the threat vector, wherein the relationship data identifies associations between the threat vector and other online elements, wherein each of the other online elements are one of: a file, a uniform resource locator, and a software application;
identifying one or more of the other online elements as a predictive network threat based at least upon an association between the threat vector and the respective other online element, the identifying one or more of the other online elements comprising:
sending a request to a relationship management system, the request identifying the threat vector; and
receiving a response from the relationship management system identifying the respective other online elements; and
providing data regarding the threat vector and the one or more of the other online elements to a firewall device using the one or more computing devices, wherein the firewall blocks network activity associated with the threat vector and the one or more of the other online elements.
|