| CPC G06F 21/6218 (2013.01) [G06F 2221/2141 (2013.01)] | 25 Claims |
|
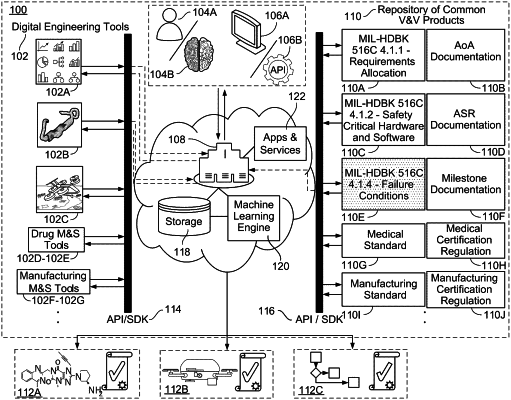
1. A computer-implemented method comprising:
receiving, from a user device and by a digital platform, a request to interact with a digital model;
determining whether a user operating the user device is authorized to access the digital platform;
in response to determining that the user is authorized to access the digital platform, generating a token that provides the user with access to the digital platform;
determining whether the request includes malicious activity;
in response to determining that the request is absent of the malicious activity, executing, using data from the request and the generated token enabling the user access to the digital platform, a digital thread that executes one or more operations using one or more digital tools and the digital model, wherein executing the digital thread comprises executing, across a multi-cellular environment, the one or more operations using the one or more digital tools on the digital model, each cell of the multi-cellular environment executing one or more of the one or more operations upon the digital model; and
providing data indicative of the one or more operations executing the digital thread to the user device for presenting on a user interface of the user device.
|