| CPC G06F 21/602 (2013.01) [H04L 9/50 (2022.05)] | 7 Claims |
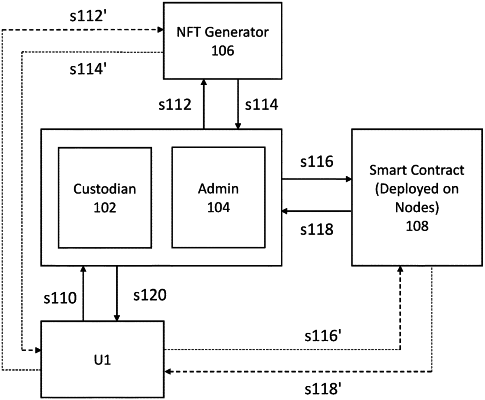
|
1. A system, the system comprising:
a processor; and
a memory storing instructions that, when executed by the processor, are configured to cause the system to:
receive, from a first entity, a cryptographic data structure configured to identify a physical item stored in a secured physical location that encloses the physical item, wherein the cryptographic data structure is a non-fungible token that stores one or more attributes describing the physical item;
secure the cryptographic data structure on a public data structure,
wherein the public data structure is a distributed ledger in a decentralized network,
a smart contract secures the cryptographic data structure on the public data structure, such that that the cryptographic data structure cannot be transferred on the public data structure unless a verification condition is satisfied,
the verification condition is satisfied when the smart contract receives a Plurality of fungible cryptographic items or receives a request indicating the Plurality of fungible cryptographic items are associated with a single wallet address,
the Plurality of fungible cryptographic items are fungible tokens that are associated with the non-fungible token and the physical item, and
the fungible tokens are configured to, when held by a single entity, collectively represent a right of access to the physical item;
receive, from a second entity that is different from the first entity, a request to transfer the cryptographic data structure; and
in response to receiving the request and the verification condition being satisfied, transmit to the second entity the cryptographic data structure, the cryptographic data structure being configured to be used by the second entity as a security credential to retrieve the physical item from the secured physical location enclosing the physical item.
|