| CPC G06F 21/32 (2013.01) [G06F 21/31 (2013.01); G06V 40/161 (2022.01); G10L 25/51 (2013.01)] | 20 Claims |
|
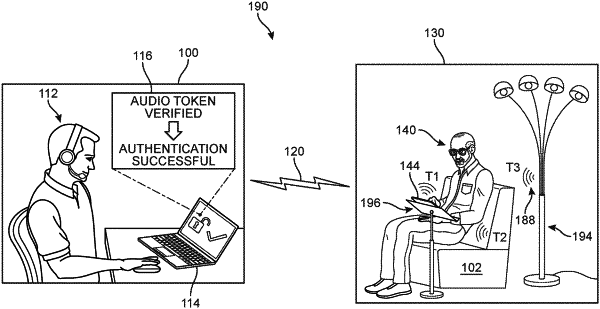
1. A computer-implemented method of verifying an authenticity of video in order to protect user resources, the method comprising:
obtaining, at a cloud-based authentication system, a first audio token from a first computing device stationed in a first physical space;
receiving, at the authentication system and from the first computing device, a request to access a secured resource of a first user while video is streaming from the first computing device to the authentication system;
transmitting, from the authentication system and in response to the request, a first control signal to the first computing device, the first control signal including a first audio signal;
obtaining, at the authentication system, first audio data captured by a microphone of the first computing device around the time playback of the first audio signal by a speaker of first computing device was to have occurred;
determining, at the authentication system, that the first audio data includes a feature set that matches a feature set of the audio token;
verifying, in response to the audio features matching, an authenticity of the video;
thereby granting the first user access to the secured resource for which the first user is authorized;
obtaining, at the authentication system, a second audio token from a second computing device stationed in a second physical space different from the first physical space; and
storing the first audio token and the second audio token in a user accounts database record for the first user, wherein the first audio token includes audio generated by a reflection of soundwaves from surfaces around the location of the first computing device when a second audio signal is produced, the second audio token includes audio generated by a reflection of soundwaves from surfaces around the location of the second computing device, and the first audio signal and the second audio signal differ.
|