| CPC H04L 9/0877 (2013.01) [G06F 9/4406 (2013.01); H04L 9/0825 (2013.01); H04L 9/0844 (2013.01); H04L 2209/127 (2013.01)] | 20 Claims |
|
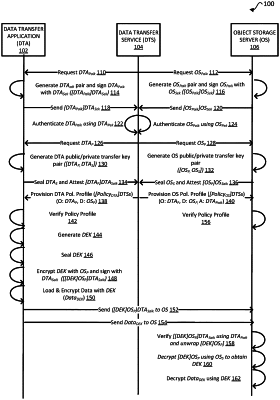
1. A computer-implemented method, comprising:
receiving, in a secure environment of a storage server, a policy profile from a data transfer service, the policy profile including an origination key and a destination key, and the origination key corresponding to a public transfer key of a data transfer application that is associated with a transfer of particular sensitive data from the data transfer application to the storage server;
verifying, by the storage server in the secure environment, the policy profile based at least in part on determining that the destination key corresponds to a public transfer key of the data transfer application;
receiving, by the storage server, a signed encrypted data encryption key from the data transfer application;
receiving, by the storage server, encrypted data from the data transfer application for subsequent decryption of the encrypted data;
verifying, by the storage server, the signed encrypted data encryption key originated from the data transfer application based at least in part on determining that the signed encrypted data key is signed with a private attestation identity key that corresponds to a public attestation identity key of the data transfer application; and
decrypting, by the storage server, the encrypted data using a private transfer key of the storage server, the decrypted data corresponding to the particular sensitive data.
|