| CPC H04L 63/20 (2013.01) [H04L 63/105 (2013.01)] | 16 Claims |
|
1. A computerized method for remediating data assets on one or more service (SaaS) platforms, the method comprising:
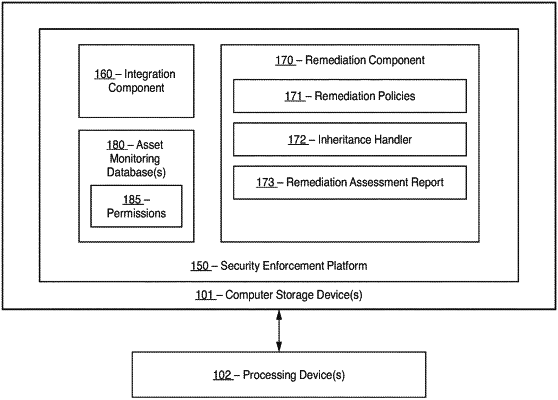
providing access to a security enforcement platform;
integrating one or more SaaS accounts provided via one or more SaaS platforms with the security enforcement platform, each of the one or more SaaS accounts storing data assets;
maintaining one or more databases on the security enforcement platform to remotely track the permissions for the data assets stored on the one or more SaaS platforms;
receiving, by the security enforcement platform, inputs specifying a remediation policy relating to the data assets, wherein the security enforcement platform utilizes the permissions stored in the one or more databases to identify a target set of data assets for remediation;
in response to determining that one or more data assets within the target set of data assets include inherited permissions from a parent drive or a parent directory, remotely executing an analysis on the security enforcement platform to identify one or more collateral data assets, wherein the one or more collateral assets correspond to a subset of data assets stored on the one or more SaaS accounts that fall outside the remediation policy but which would be affected if the permissions of the parent directory or the parent drive were changed;
presenting, by the security enforcement platform, one or more inherency handling options that enable a user to refine the remediation policy according to:
a first remediation setting that causes the one or more collateral data assets to be included in the target set of data assets to be remediated; and
a second remediation setting that excludes the one or more collateral data assets and the one or more data assets having the inherited permissions from the target set of data assets to be remediated; and
executing, by the security enforcement platform, the remediation policy according to the first remediation setting or the second remediation setting based on a selection of the one or more options, wherein executing the remediation policy includes transmitting commands over a network to the one or more SaaS platforms to modify the permissions corresponding to the target set of data assets identified by the remediation policy.
|