| CPC H04L 63/0263 (2013.01) [H04L 63/1433 (2013.01)] | 23 Claims |
|
1. A method for providing dynamic network traffic policies, comprising:
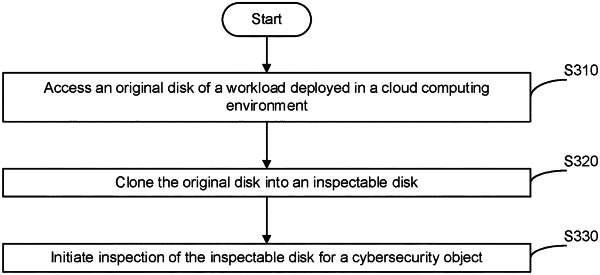
generating an inspectable disk from an original disk of a workload, the workload deployed in a cloud computing environment, wherein the cloud computing environment has a firewall connected to an untrusted network;
inspecting the inspectable disk for a cybersecurity object, the cybersecurity object indicating a cybersecurity risk;
detecting the cybersecurity risk on the workload based on the cybersecurity object; and
configuring the firewall to filter network traffic to the workload based on the detected cybersecurity risk.
|