| CPC H04L 41/0627 (2013.01) [G06N 20/00 (2019.01); H04L 41/064 (2013.01); H04L 41/0856 (2013.01); H04L 41/5041 (2013.01); H04L 43/065 (2013.01); H04L 43/0817 (2013.01); H04L 43/10 (2013.01)] | 11 Claims |
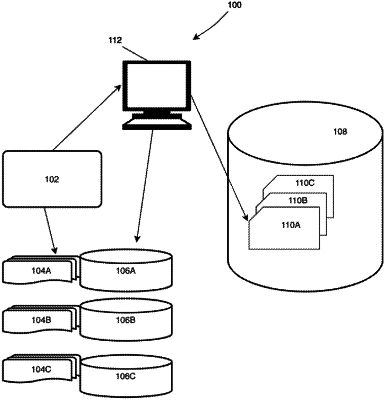
|
1. A computer implemented method of automated cause analysis for network-entity anomalous activity, the method executed on a processor, the method comprising:
storing a first backup slice of a network entity;
collecting a first set of system events associated with a network-entity activity for a first time period;
determining a first activity pattern of the network entity from the first set of system events, wherein the first activity pattern characterizes a safe operation of the network entity;
detecting a change of a configuration parameter of the network entity;
storing a second backup slice of the network entity in response to the detected change in the configuration parameter;
collecting a second set of system events associated with the network-entity activity for a second time period, wherein the second time period starts when a change of a configuration parameter is detected or when the second backup slice is stored;
detecting an anomalous activity of the network entity based on the second set of system events;
determining network-entity configuration parameters in effect at the first time period corresponding to the first backup slice and at the second time period corresponding to the second backup slice;
determining a substantial cause of the detected anomalous activity, wherein determination of the substantial cause is performed by determining changed configuration parameters between the first and second backup slices.
|