| CPC G06Q 10/10 (2013.01) [G06F 9/44505 (2013.01); G06F 9/54 (2013.01); G06F 9/547 (2013.01); G06F 16/258 (2019.01); G06F 16/9558 (2019.01); G06F 16/9562 (2019.01); G06F 18/24 (2023.01); G06F 21/53 (2013.01); G06F 21/602 (2013.01); G06F 21/604 (2013.01); G06F 21/6227 (2013.01); G06F 21/6245 (2013.01); G06F 40/103 (2020.01); G06F 40/174 (2020.01); G06F 40/18 (2020.01); G06N 3/02 (2013.01); G06N 5/025 (2013.01); G06N 20/00 (2019.01); G06Q 20/382 (2013.01); G06Q 20/4014 (2013.01); G06Q 30/0185 (2013.01); G06Q 30/0206 (2013.01); G06Q 30/0601 (2013.01); G06Q 30/0613 (2013.01); G06Q 30/0619 (2013.01); G06Q 30/0637 (2013.01); G06Q 30/0643 (2013.01); G06Q 40/02 (2013.01); G06Q 40/03 (2023.01); H04L 9/0825 (2013.01); H04L 63/0435 (2013.01); H04L 63/08 (2013.01); H04L 63/0815 (2013.01); H04L 63/102 (2013.01); H04L 63/123 (2013.01); H04L 63/166 (2013.01); H04L 63/168 (2013.01); H04L 67/01 (2022.05); G06F 8/65 (2013.01); G06F 8/71 (2013.01); G06F 2221/2107 (2013.01); G06K 7/1417 (2013.01); G06Q 50/265 (2013.01); G06Q 2220/00 (2013.01); H04L 9/0822 (2013.01)] | 20 Claims |
|
1. A method comprising:
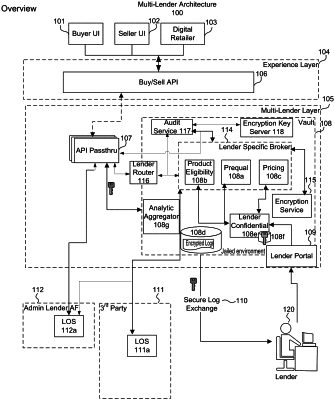
receiving, at a server, one or more rule sets or executable logic from each of at least one entity;
storing the one or more rule sets or executable logic in a jailed and self-contained environment comprising a vault within the server, the one or more rule sets or executable logic being encrypted with an entity-specific key upon receipt of the one or more rule sets or executable logic for each such entity, or encrypted at a predetermined later time for each such entity, with an entity-specific key, wherein the rule sets or executable logic for each such entity are accessible in the jailed and self-contained environment by at least one entity-specific routing component dedicated for each such entity;
receiving, at the server, a request from a particular user via a user-facing application, the request relating to an inquiry associated with a product provided by each of the at least one entity, a response to the inquiry being determined autonomously for a respective entity based on the respective rule sets or executable logic for each respective entity;
decrypting autonomously, inside of the jailed and self-contained environment in the server, the rule sets or executable logic for one or more of the at least one entities, by the at least one entity-specific routing component for the respective at least one entity, wherein each one of the at least one entity-specific routing components corresponds to a particular entity of the at least one entity;
applying, autonomously by the at least one entity-specific routing component for each respective entity, one or more rule sets or executable logic to determine a respective response to the inquiry;
generating encrypted outputs autonomously in an entity-agnostic format by the at least one entity-specific routing component within the jailed and self-contained environment based on the respective responses by compiling the respective responses into a universally encrypted lender agnostic composite payload; and
transmitting said encrypted outputs from said server through an application protocol interface, sending the encrypted outputs onwards toward the user-facing application with segregated user sessions, and decrypting the outputs only in the particular user session of said application, such that the contents of the decrypted outputs are only visible to the particular user
wherein the vault is encrypted by the entity-specific key such that an administrator of the server cannot view its components.
|