| CPC G06F 40/18 (2020.01) [G06F 18/24 (2023.01); G06F 21/602 (2013.01)] | 20 Claims |
|
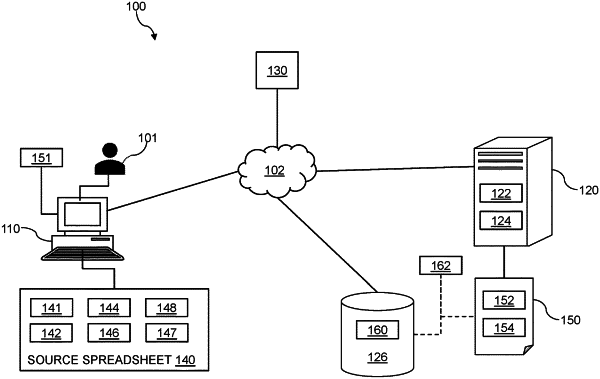
1. A method for securely processing disparate data sets according to functionality of a spreadsheet, the method comprising:
receiving a source spreadsheet from a user, the source spreadsheet including:
a first input data set;
one or more formulas configured to manipulate the first input data set thereby generating a first output data set; and
one or more directives associated with the source spreadsheet, the one or more directives describing at least one of the first input data set, the one or more formulas, and the first output data set, the one or more directives defining functionality of the source spreadsheet, and the one or more directives specifying at least one of generation, manipulation, and arrangement of cells to be performed at a later time;
compiling the source spreadsheet including translating data within the source spreadsheet into an intermediary form and extracting the one or more directives;
writing output of the compiling of the source spreadsheet to a file;
encrypting the file with an encryption key associated with the user thereby creating an encrypted file;
reading and executing the encrypted file using a runtime associated with the user, the runtime operating according to one or more rules identifying one or more permissible combinations for execution of the one or more directives and specifying an order and a context for execution of the one or more directives; and
transmitting an output from reading and executing the encrypted file using the runtime to a user device over a data network.
|