| CPC G06F 21/62 (2013.01) [H04L 63/107 (2013.01); G06F 2221/2111 (2013.01)] | 19 Claims |
|
1. A computer program product comprising a non-volatile computer readable medium and non-transitory program instructions embodied therein, the program instructions being configured to be executable by a processor to cause the processor to perform operations comprising:
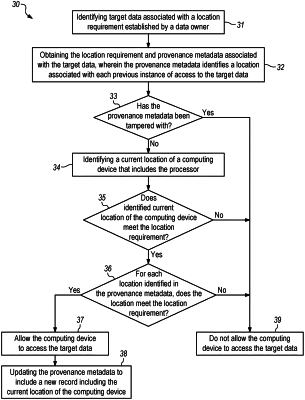
identifying target data associated with a location requirement established by a data owner;
obtaining the location requirement and provenance metadata associated with the target data;
determining whether the provenance metadata has been tampered with, wherein the provenance metadata identifies a location associated with each previous instance of access to the target data, wherein the provenance metadata is determined to have been tampered with in response to identifying one or more location in the provenance metadata that does not meet the location requirement associated with the target data;
identifying a current location of a computing device that includes the processor;
determining whether the identified current location of the computing device meets the location requirement;
determining, for each location identified in the provenance metadata, whether the location meets the location requirement;
allowing the computing device to access the target data only in response to determining that the current location and each location identified in the provenance metadata meet the location requirement; and
updating the provenance metadata to include a new record including the current location of the computing device in response to allowing the computing device to access the target data.
|