| CPC G06F 21/577 (2013.01) [G06F 21/54 (2013.01); G06F 21/562 (2013.01); G06F 21/566 (2013.01); G06F 21/64 (2013.01)] | 19 Claims |
|
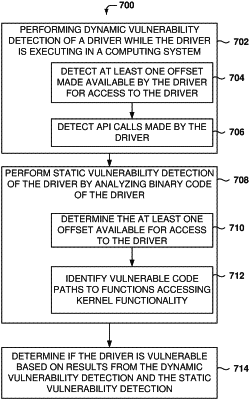
1. A computer-implemented method comprising:
performing dynamic vulnerability detection of a driver while the driver is executing in a computing system, the dynamic vulnerability detection comprising:
detecting at least one offset made available by the driver for access to the driver; and
detecting application programming interface (API) calls made by the driver;
performing static vulnerability detection of the driver by analyzing binary code of the driver, the static vulnerability detection comprising:
determining the at least one offset available for access to the driver; and
identifying vulnerable code paths to functions accessing kernel functionality;
determining if the driver is vulnerable based on results from the dynamic vulnerability detection and the static vulnerability detection; and
automatically disabling the driver in the computer system for access by other programs based on the determining that the driver is vulnerable.
|