| CPC A61N 1/3904 (2017.08) [A61B 5/02438 (2013.01); A61N 1/046 (2013.01); A61N 1/0484 (2013.01); A61N 1/3987 (2013.01); A61N 1/3993 (2013.01); G06F 21/33 (2013.01); H04L 9/3268 (2013.01); H04L 63/0823 (2013.01); A61B 5/361 (2021.01); A61B 5/363 (2021.01); A61B 5/6805 (2013.01); A61B 5/74 (2013.01); A61N 1/37258 (2013.01); A61N 1/3925 (2013.01)] | 10 Claims |
|
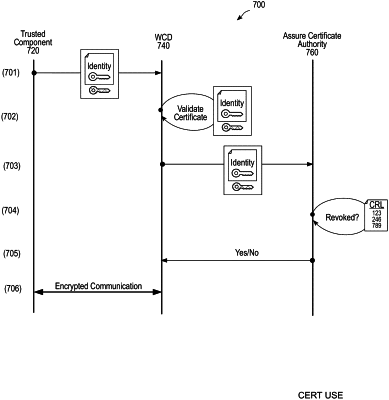
1. A method for communicating with a patient monitoring medical device system, comprising:
issuing a certificate signing request (CSR) to a certificate authority for attestation, the certificate signing request including a public key associated with a trusted device;
receiving from the certificate authority a signed security certificate, wherein the signed security certificate includes information that identifies a set of permissions that are authorized to the trusted device;
initiating a communication session between the trusted device and a secure component of the patient monitoring medical device system;
transmitting the signed security certificate to the secure component for verification;
authorizing the set of permissions to the trusted device based on the information; and
upon confirmation that the signed security certificate has been verified, authorizing communications between the trusted device and the secure component using the communication session.
|