| CPC H04L 63/1425 (2013.01) [G06N 20/00 (2019.01); H04L 63/0236 (2013.01)] | 20 Claims |
|
1. An information security system, comprising:
a plurality of network devices, wherein each network device is configured to provide access to data for a plurality of users; and
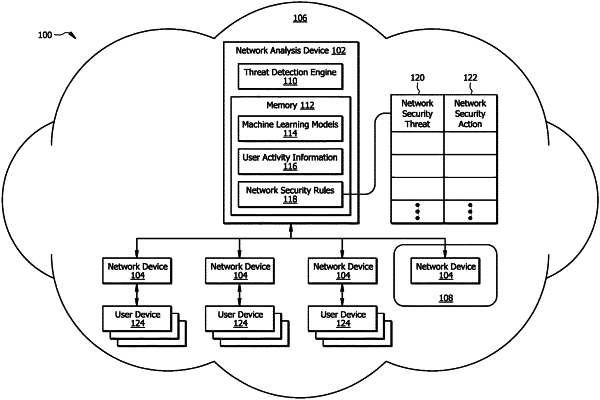
a network analysis device in signal communication with the plurality of network devices, and comprising:
a memory operable to store:
network security rules, wherein the network security rules map network security threats to network security actions, wherein the network security actions comprise instructions for modifying device settings; and
a processor operably coupled to the memory, and configured to:
receive user activity information from a network device, wherein the user activity information comprises information about user interactions with the network device for the plurality of users;
input the user activity information into a first machine learning model, wherein the first machine learning model is configured to:
receive user activity information; and
output a set of bad actor candidates based on the user activity information, wherein the set of bad actor candidates identifies one or more users from among the plurality of users;
receive the set of bad actor candidates from the first machine learning model;
filter the user activity information based on the set of bad actor candidates, wherein filtering the user activity information comprises removing user activity information for users that are not members of the set of bad actor candidates;
input the filtered user activity information into a second machine learning model, wherein the second machine learning model is configured to:
receive the filtered user activity information; and
output system exposure information based on the user activity information, wherein the system exposure information identifies one or more network security threats;
identify one or more network security actions within the network security rules based on the one or more network security threats identified in the system exposure information;
execute the one or more network security actions, wherein the one or more network security actions include modifying the settings of the network device;
periodically collect additional user activity information from the network device and use the additional user activity information to identify additional network security threats;
identify one or more additional network security actions based on the identified additional network security threats; and
execute the one or more additional network security actions;
wherein the one or more network security actions are identified using the one or more network security threats as a search token to search the network security rules;
wherein the first machine learning model is a multi-layer perception neural network model; and
wherein the first machine learning model is stored and trained by a device that is external to the network analysis device.
|