| CPC H04L 63/1416 (2013.01) [G06F 16/9024 (2019.01); G06N 20/00 (2019.01); H04L 61/4511 (2022.05)] | 17 Claims |
|
1. A computer-implemented method for identifying suspicious communication network assets, the method comprising:
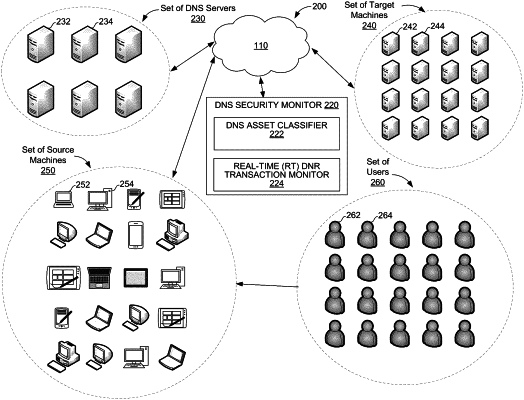
accessing network traffic (NT) data that encodes at least one domain name resolution (DNR) transaction associated with a plurality of addresses that includes a plurality of domain name system (DNS) addresses and at least one target address;
employing the NT data to generate a graph data structure including a plurality of nodes with each node representing an address from the plurality of addresses and a plurality of edges, the plurality of nodes including a plurality of DNS nodes with each DNS node representing a DNS address from the plurality of DNS addresses and at least one target node representing the at least one target address, and at least one edge from the plurality of edges connecting each of the plurality of DNS nodes to at least one of the at least one target node based on the at least one DNR transaction;
identifying a first portion of the plurality of nodes, each node included in the first portion of the plurality of nodes is ground-truth labeled as a suspicious node;
identifying a second portion of the plurality of nodes, each node included in the second portion of the plurality of nodes is unclassified; and
assigning a node risk score to each node included in the second portion of the plurality of nodes, based on a comparison of the nodes included in the second portion of the plurality of nodes and each node included in the first portion of the plurality of nodes;
based on the node risk score assigned to each of the plurality of nodes in the second portion, identifying a third portion of the plurality of nodes;
classifying each address of the plurality of addresses that is represented by a node included in the third portion of the plurality of nodes as a suspicious address; and
providing an indication of at least one address of the plurality of addresses that has been classified as a suspicious address.
|