| CPC G06F 21/6218 (2013.01) [G06F 16/137 (2019.01); G06F 16/285 (2019.01); G06F 16/93 (2019.01); G06F 21/64 (2013.01); G06N 20/00 (2019.01); H04L 9/3265 (2013.01); H04L 41/20 (2013.01); H04L 41/22 (2013.01); H04L 63/08 (2013.01); H04L 63/0838 (2013.01); H04L 63/101 (2013.01); H04L 63/102 (2013.01); H04L 63/1408 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01); H04L 63/205 (2013.01)] | 20 Claims |
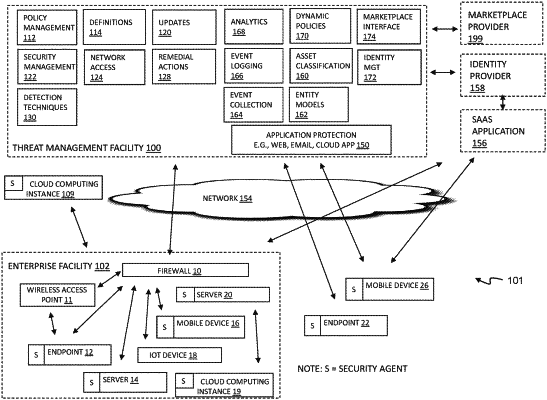
|
1. A computer program product comprising computer executable code embodied in a non-transitory computer readable medium that, when executing on one or more computing devices, performs the steps of:
receiving a request for a remote resource from a compute instance in an enterprise network, the remote resource requiring authentication;
receiving a risk score for the compute instance, the risk score based on a risk assessment for the compute instance by a local security agent executing on the compute instance;
selecting an authentication model from a number of authentication models for the remote resource, wherein:
the number of authentication models provide different authentication factors for the compute instance based on a level of security risk for the compute instance indicated by the risk score,
the authentication model includes one or more authentication factors for authentication to the remote resource, and
selecting the authentication model includes selecting the authentication model based on the risk score for the compute instance;
causing the compute instance to authenticate to the remote resource to establish an authenticated session according to the authentication model;
updating the risk score for the compute instance; and
based on the updated risk score for the compute instance, deauthenticating the authenticated session and selecting a new authentication model from the number of authentication models for use in authenticating to the remote resource.
|