| CPC G06F 21/577 (2013.01) [G06F 2221/033 (2013.01)] | 10 Claims |
|
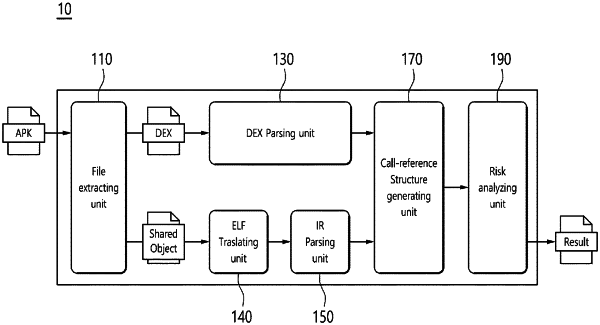
1. A method for evaluating a risk of data leakage in a mobile application, the method comprising:
extracting a DEX (Dalvik Executable) file and a so (Shared Object) file by decompressing an APK file of the mobile application;
extracting DEX code information from the DEX file by parsing the DEX file;
translating a content of the so file into IR (Intermediate Representation);
extracting IR code information from the translated IR;
generating a call-reference structure between the DEX file and the so file by processing the extracted DEX code information and the extracted IR code information; and
outputting weakness information according to a risk designated in advance based on the generated call-reference structure,
wherein the outputting the weakness information comprises:
comparing a list of specific functions and methods classified according to risks with the generated call-reference structure to inspect whether a corresponding function exists;
when the corresponding function exists in the generated call-reference structure, tracking and generating all reachable paths;
searching whether a point moving to an I/O (Input/Output, L) of a system exists;
when the point moving to the I/O exists, producing the weakness information according to the risk designated in advance; and
documenting the weakness information according to a standard format and outputting the documented weakness information as a final output.
|