| CPC G06F 16/355 (2019.01) [G06F 16/90344 (2019.01); G06F 17/17 (2013.01); G06F 18/22 (2023.01)] | 19 Claims |
|
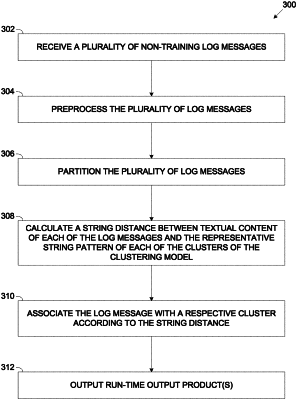
1. A computer implemented method of detecting at least one anomaly within a plurality of non-training log messages during run-time, by using a clustering model targeting a predefined source of the run-time messages, comprising:
using at least one processor for:
calculating a string distance between a textual content of each of a plurality of non-training log messages, in run-time, and a representative string pattern of each of a plurality of clusters of a clustering model targeting a predetermined certain source of messages, wherein said clustering model is constructed during a training phase, using a plurality of training messages which are selected, constructed and adapted to represent non-training messages originated by said predetermined certain source which is targeted for log message analysis during a run-time phase;
detecting at least one log message of the plurality of non-training log messages for which the string distance to the representative string pattern of each of the plurality of clusters exceeds a predefined threshold; and
generating an alert indicative of the at least one detected log message as at least one suspected anomaly.
|