| CPC H04W 12/122 (2021.01) [H04W 64/003 (2013.01); H04L 63/20 (2013.01); H04W 88/08 (2013.01)] | 20 Claims |
|
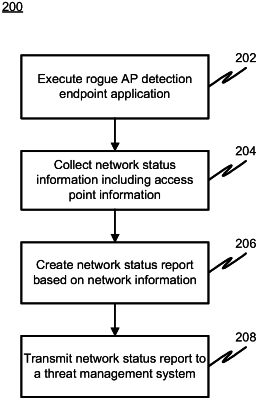
1. A computer-implemented method, comprising:
sending, from a threat management system, one or more parameters to one or more selected access points from a set of one or more access points registered with the threat management system, wherein the one or more parameters, when applied at the one or more selected access points, modify an operational aspect of the one or more selected access points;
after the sending, receiving, at the threat management system, from one or more endpoint devices one or more status messages, wherein each status message includes access point information about one or more access points that the endpoint device connects to, wherein the one or more access points include at least one selected access point and wherein the access point information is indicative of a respective operational parameter of the one or more access points;
detecting that the operational parameter of a particular access point of the one or more access points does not match the operational aspect; and
based on the detecting, performing, by the threat management system, one or more actions to restrict the particular access point.
|