| CPC H04L 9/0872 (2013.01) [G06F 21/645 (2013.01); H04L 9/0894 (2013.01); H04L 9/321 (2013.01); H04L 9/3236 (2013.01); H04L 9/3297 (2013.01)] | 21 Claims |
|
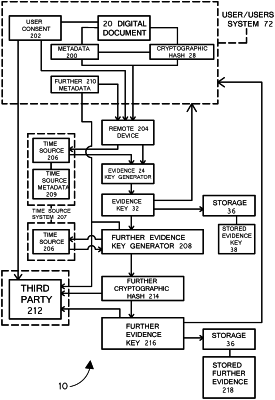
1. A computer-implemented method for evidencing the existence of a digital document comprising the steps of:
A. obtaining metadata of a digital document in a user's system;
B. obtaining a cryptographic hash of the digital document via the user's system;
C. sending the metadata and the cryptographic hash from the user's system to a remote device; or sending the metadata and the cryptographic hash to the remote device over the internet;
D. receiving the metadata and the cryptographic hash at the remote device;
E. requesting a time stamp from a time source;
F. receiving the time stamp at the remote device from the time source, wherein the remote device does not comprise the time source, and wherein the time stamp is based upon the time that the remote device receives the metadata and the cryptographic hash;
E. combining the metadata, the cryptographic hash, and the time stamp in an evidence key generator to generate an evidence key;
F. storing the evidence key to provide a stored evidence key;
G. generating a further cryptographic hash of the evidence key in a further evidence key generator to form a further evidence key; and
H. storing the further evidence key to form a stored further evidence key,
wherein during the method the digital document remains within the user's system.
|