| CPC H04L 9/0869 (2013.01) [G06F 21/602 (2013.01); G06F 21/6245 (2013.01); H04L 9/0894 (2013.01); H04L 63/0428 (2013.01); H04L 63/0435 (2013.01)] | 19 Claims |
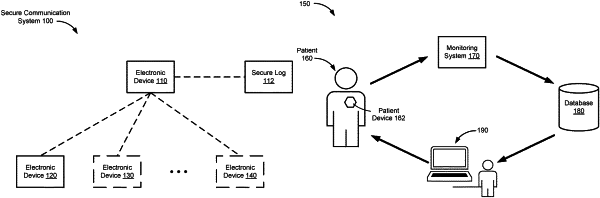
|
1. A method performed at a first electronic device, the method comprising:
storing a privacy table at the first electronic device, the privacy table comprising random numbers;
transmitting the privacy table to a second electronic device over an encrypted channel, wherein the second electronic device is distinct from the first electronic device;
receiving a first message for transmission to the second electronic device;
generating a map based on the privacy table, the map including instructions on how to use the privacy table to generate a primary key;
generating the primary key based on the map and the privacy table;
encrypting the first message using the primary key to form an encrypted first message;
transmitting the map and the encrypted first message to the second electronic device, enabling the second electronic device to decrypt the encrypted first message by:
recreating the primary key based on the map and the privacy table; and
decrypting the encrypted first message using the recreated primary key;
receiving a second message for transmission to the second electronic device;
generating a new map, which is distinct from the map;
generating a new primary key based on the new map and the privacy table, wherein the new primary key is distinct from the primary key;
encrypting the second message using the new primary key to form an encrypted second message; and
transmitting the new map and the encrypted second message to the second electronic device, enabling the second electronic device to decrypt the encrypted second message by:
recreating the new primary key based on the new map and the privacy table; and
decrypting the encrypted second message using the recreated new primary key.
|