| CPC H04L 9/0861 (2013.01) [G06F 9/45558 (2013.01); G06F 2009/45587 (2013.01)] | 20 Claims |
|
1. A system, comprising:
one or more computing devices;
wherein the one or more computing devices include instructions that upon execution on or across the one or more computing devices cause the one or more computing devices to:
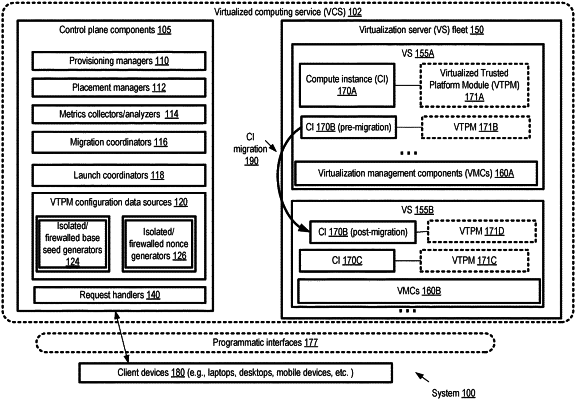
transmit, prior to a launch of a compute instance at a first virtualization server of a virtualized computing service: (a) an entropy source value from a first isolated control plane component of the virtualized computing service to one or more virtualization management components of the first virtualization server and (b) a nonce and a first counter value from a second isolated control plane component of the virtualized computing service to the one or more virtualization management components of the first virtualization server, wherein the entropy source value is not accessible to the second isolated control plane component, and wherein the nonce and the first counter value are not accessible to the first isolated control plane component;
store an updated counter value at a storage device associated with the first virtualization server after performing one or more cryptographic operations at the first virtualization server, wherein the updated counter value is obtained from the first counter value, wherein the one or more cryptographic operations include generation of a particular cryptographic key utilized at the compute instance, wherein the particular cryptographic key is generated by a first virtualized Trusted Platform Module (VTPM) assigned to the compute instance and initialized at the first virtualization server, and wherein the first VTPM is initialized using at least the entropy source value, the nonce and the first counter value; and
perform, at a second virtualization server selected as a migration destination for the compute instance, one or more additional cryptographic operations after the compute instance is migrated to the second virtualization server, wherein the one or more additional cryptographic operations include generation of another cryptographic key used at the compute instance, wherein the other cryptographic key is generated by a second VTPM assigned to the compute instance and initialized at the second virtualization server, and wherein the second VTPM is initialized using at least the entropy source value, the nonce and the updated counter value.
|