| CPC H04L 63/30 (2013.01) | 20 Claims |
|
1. A method for triggering lawful interception, LI, in a communication network, the method comprising:
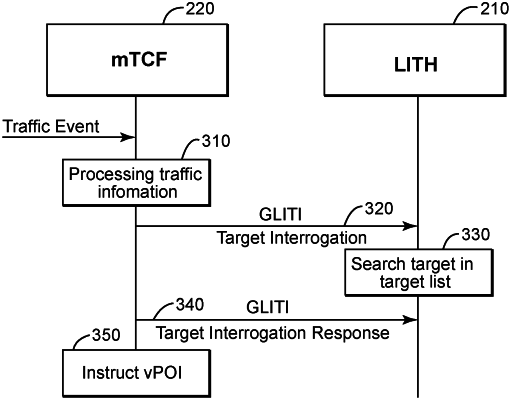
implementing a triggering control function, TCF, as two entities:
an LI target handler, LITH, which meets LI security requirements for holding and processing sensitive information, maintains an LI target list, and
a modified TCF, mTCF, which does not have to meet the LI security requirements, triggers a point of interception, POI, linked to a network function instance, NFI, to start intercepting specific target's communications occurring when the NFI is executed; and
providing a generic LI triggering interface, GLITI between the LITH and the mTCF to enable the mTCF to interrogate the LITH regarding whether an entity using the NFI is a specific target of LI.
|