| CPC H04L 63/20 (2013.01) [G06F 40/30 (2020.01); G06N 20/00 (2019.01)] | 17 Claims |
|
1. A system comprising:
one or more processing units; and
a computer-readable storage medium having computer-executable instructions stored thereupon, which, when executed by the one or more processing units, cause the one or more processing units to:
receive, as part of a training data set, a plurality of labeled documents and mitigation actions that were recommended or performed to resolve a security issue indicated in the plurality of labeled documents;
learn, for a model that implements natural language processing and using the training data set, (i) a mapping between one or more text segments and an individual notable security feature and (ii) a mapping between the individual notable security feature and a mitigation action;
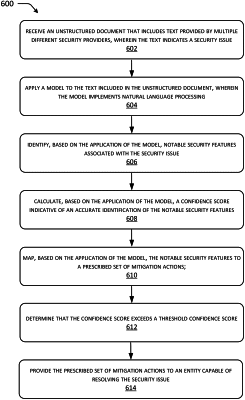
receive an unstructured document that includes text provided by multiple different security providers, wherein the text included in the unstructured document indicates the security issue via multiple different alerts generated by the multiple different security providers based on at least one detected event;
apply the model to the text included in the unstructured document;
identify, based on the application of the model, notable security features associated with the security issue;
calculate, based on the application of the model, a confidence score indicative of an accurate identification of the notable security features;
map, based on the application of the model, the notable security features to a prescribed set of mitigation actions;
determine that the confidence score exceeds a threshold confidence score; and
based on the determination that the confidence score exceeds the threshold confidence score, provide the prescribed set of mitigation actions to at least one entity capable of resolving the at least one security issue.
|